Recent posts
Complete steps to configure passwordless SSH login and avoid entering the passphrase every time:
Complete steps to configure password less SSH login and avoid entering the pass…
Read moreIoT and its Impact on Software Development
The application and use of IoT are increasing at an amazing rate all around t…
Read moreWipro WILP Most Commonly AskedTechnical Interview Questions?
Prepare these questions for TR. tell me about your self?? tell me about your p…
Read moreTypes of web application attacks
♀️ *Cross-Site Scripting (XSS)* – The goal of this threat could be to inject co…
Read moreWhatsApp just changed its terms and conditions. You have just one month to decide.
Whatsapp will collect usage and log information , phone number, mobile operato…
Read morePython Random Password Generating Mini Project
import random import math alpha = "abcdefghijklmnopqrstuvwxyz" n…
Read moreGrab this opportunity to learn Python with 40 hours of free access from 8 AM IST on Saturday 31st October 2020
Grab this opportunity to learn Python with 40 hours of free access from 8 AM IS…
Read moreFacebook Information Gathering | Kali linux Tool | FBI|
Facebook information Gathering FBI is an accurate facebook account information…
Read moreKannur University Bsc Computer Science Previous Question Papers
MMCCS.XYZ Domain name is expired. So Click Here Kannur University BSc Comput…
Read moreBooleans in Java
Java has a simple type, called boolean , for logical values. It can have only o…
Read moreCharacter Data Type in Java
In Java , the data type used to store characters is ' char '. However,…
Read moreData Types in Java Long/Double [P-1]
Long Long is a signed 64-bit type and is useful for those occasions where an …
Read moreOne-Dimensional Arrays in Java
One-Dimensional Arrays one-dimensional array is, essentially, a list of like-ty…
Read moreJava Program to find GCD of 2 Numbers
Java Program to find gcd of 2 numbers What is gcd ? "In mathematics, the …
Read moreJava Program to accept three numbers and find Largest and Second largest numbs.
Java Program to identify largest and second largest number Using if else large …
Read moreJava Programming
What is – Java is a programming language and a pla…
Read moreHow to increase Virtual RAM to Make Your System Faster
1. Press and Hold down the 'Windows' Key and Press the 'Pa…
Read moreTop 10 Common Hacking Techniques All Beginners Should Know About
10. Keylogger Keylogger is a simple software that records the key sequ…
Read moreHow To Remove Shortcut Virus From Your Pc
✅ Method 1. - Clean up and remove Shortcut Virus by CMD - 1. Click …
Read moreKannur University Bsc Computer Science
Introducing New Website for Kannur university Bsc Computer Science Students. h…
Read moreC program to print Largest and Second largest among Three numbers
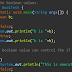
#include<stdio.h> #include<conio.h> int main() { clrscr(); …
Read moreC program to print Prime Number between any two given limit
#include<stdio.h> #include<conio.h> int main() { int l,u,i,x;…
Read moreWinrar Getinto pc Download link
Download WinRAR 5.61 Technical Setup Details Before Starting free WinR…
Read moreBottom Ad [Post Page]
Search This Blog
Recent Posts
Help Center
About Me
Contact Form
Advertisement
Ads
Advertisement
Popular Posts
Types of web application attacks
Categories
Recent Posts
Most Popular




![Data Types in Java Long/Double [P-1]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEiauvy2By8wINsUpr2wjWg9nwp_mjR8ILhG5AuP94K9n-qe3u5YRWz0VERauQ8xnkeFPqF4wb3HrisPI8ZjKgyfa5spZ4EAAjcg7j9FBkVDpyY_Zg0YTOW6LZWCucteeJxHS4qWUxsbQ-9J/w72-h72-p-k-no-nu/long.png)












Social Plugin